Fabric Api Key Exploit
To get fabric api key you need to install fabric plugin from settings plug ins then restart android studio then press fabric icon complete the wizard to get a list of fabric services choose crachlytics and install it after accepting terms of crachlytics then it will ask you to make changes to your manifest and java file and build gradle.
Fabric api key exploit. Implementing api keys for authentication and authorization is often sufficient. Sep 3 2020 game version. Explore 50 integrations that make your day to day workflow more efficient and familiar. I will discuss integrating it with ionic 3 app in my next post.
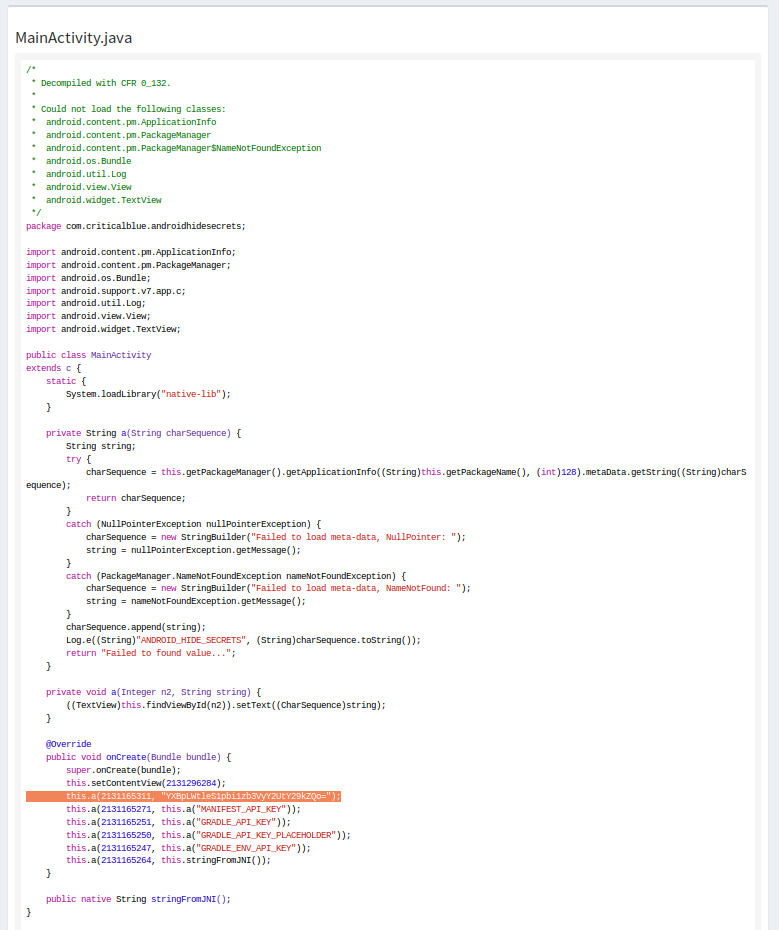
As i was developing ionic 3 application and for integrating crashelitics it requires fabric api and secret keys. Our extensive developer tools might also strike your fancy. Create an exploit in c. Core api library for the fabric toolchain.
This is separate from the fabric loader. Sign up fabrict io. Fabric api is the core library for the most common hooks and intercompatibility measures utilized by mods using the fabric toolchain. It can execute complicated scripts such as dex explorer thanks to instance caching it can run loadstrings it has a bypassed httpget which can load content from any website and adds functions to the lua environment.
Discover even more possibilities. I just wanted to share a quick method. Step to getting fabric api key and fabrict api secret. More infomation and full installation instructions can be found on the fabric website and support can be found on the fabric discord server.
This api has largely grown in capability from when the project was first released. In security standpoints often the api endpoints are overlooked. Endpoint hardening measures including key signing hashes and shared secrets are essential to integrate at the initial stages of the development of api to prevent the security loopholes. Tips to enhance the defense of apis.
3 996 356 downloads last updated. Ensure the secure communication between the apis and. However keys may be compromised if they are transmitted as part of the uniform resource identifier uri.